My view on the dedicated and so called “full” infrastructure of the App-V components has been pretty clear – its utterly useless and is always implemented for the wrong reasons. Apart from the fact that its functionality list has been degraded over-time without reason (reporting is in reality not there) – those functions that are there quite often provide a sub-standard implementation (provider policies anyway?). Currently there seem to be two main reasons – where one is mostly used as an excuse for the other – to implement this excuse of a product.
1. It provides a department, group or provider with its own dedicated infrastructure – which it can control and doesn’t have to share with any other department
2. Its fast
Unfortunately the first one can never be solved with any technical measures. Considering that most Microsoft products allow for some type of delegation of permissions (this one doesn’t) and yet there are departments who fight among each other and fail to share resources. App-V provides an easy out to allow these departments to avoid collaborating and go on with their daily operations.
Its fast is usually what keeps people away from Configuration Manager – a policy based client and deployment management tool. Policy-based quite often means waiting time – something that the ConfigMgr team has been addressing very much in the later releases since App-V was acquired by Microsoft.
Fast is good – however, fast doesn’t always mean you can deploy fast. Sometimes it means you break things fast. Quite often the side of things that can turn nasty from an operational perspective.
Lets step away from that and try to implement this. An experience an end-user wouldn’t be able to complete and something admins struggle with – with the downside that at the end of the road. Its not really properly setup.
First of all – we will be implementing this with a Windows Server 2008 R2 SP1 domain controller. The SQL-engine will be SQL Server 2012 Express with TCPIP as an allowed protocol – installed on the same server. I am avoiding Windows Server 2012 – as the road to get the basic functionality done right in the last version of the the Server OS has been to long to start over. And App-V v5 is coming.
Lets get started.
1. Ensure you do not have .NET Framework 4.0 installed. It will break things – and nobody bothered to fix the installer – see this article for yourself.
2. Setup a couple of pre-reqs. Unless you read the documentation in detail – you will not actually know about this. Recommended is to have;
- Administrative group (security group – global)
- Users Group (security group – global)
- A file-share with read-access for users and read-write access for admins.
3. Get the media and kick-off the installation. The App-V Management Server is actually at App-V 4.5 SP2 – and not 4.6 The reason seems to be that no new functionality has been brought in since App-V 4.5 from a server perspective.
3. If you haven’t done so – you will be warned during the installation. The Management Server actually depends on IIS and will require some components;
- IIS
- ASP.NET
- Security
- Windows Authentication
- IIS Management Scripts and Tools
- IIS 6 Management Compatibility
- IIS 6 Scripting Tools
- IIS 6 Management Console
- IIS 6 Metabase Compatibility
- IIS 6 WMI Compatibility
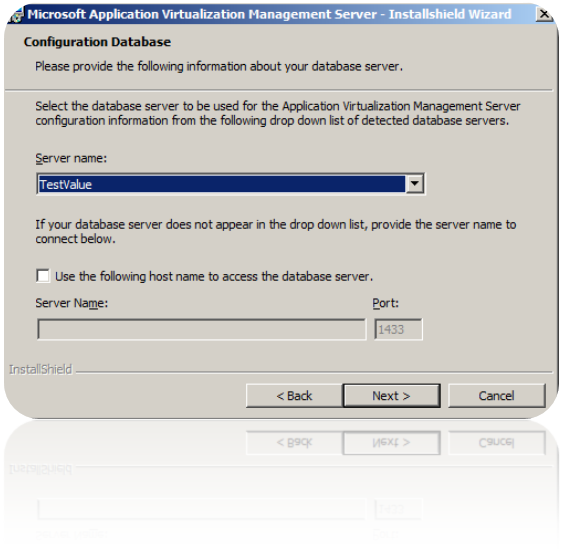
4. When you get to pick a SQL-server you might actually get to see your SQL-server in the list. If you don’t – its probably because the SQL Server doesn’t have the SQL Server Browser-service running.
5. If you setup a new database – you will be fine. If you decide to reuse an existing database – for any reason – you will get some horrible values in some tables. Once we are finished with the installation – we will verify those.
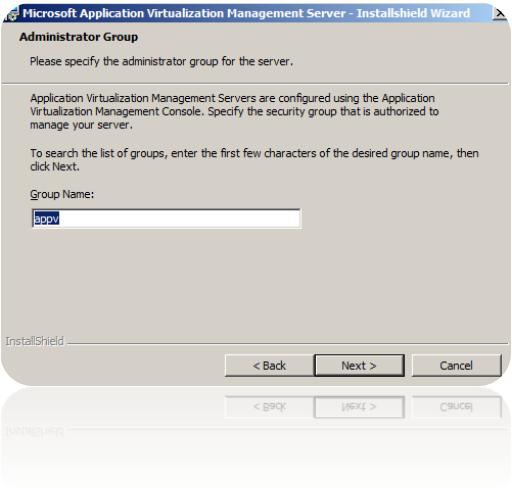
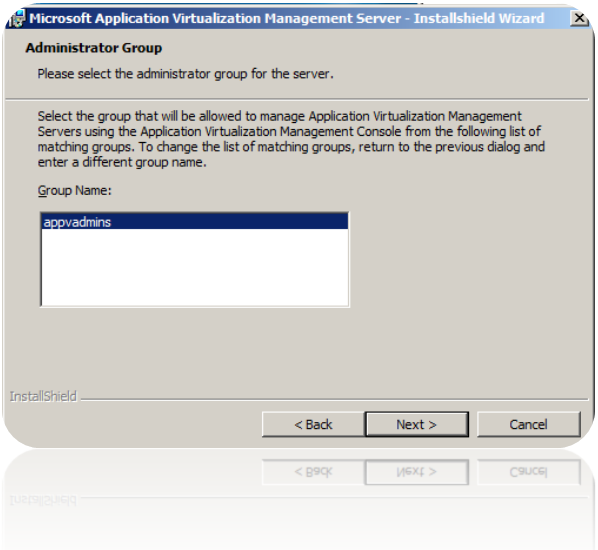
6. I can’t say why – but the way to select your two previously AD-groups are a bit unique. Nobody decided simply reuse any knowledge?
When you click next – you will see a list of possible options of active directory groups.
Weird way go about this…
Click next, rinse and repeat for the App-V Users group.
The App-V Admins group will be the people who have access to administrate the server. App-V users will have access to connect to the server. Usually – we set a pretty wide-group, such as Domain Users for the App-V Users group. Or a group containing all Domain Users from all domains. Well – you can’t get any applications if you are not part of this group. Not even if you are an admin.
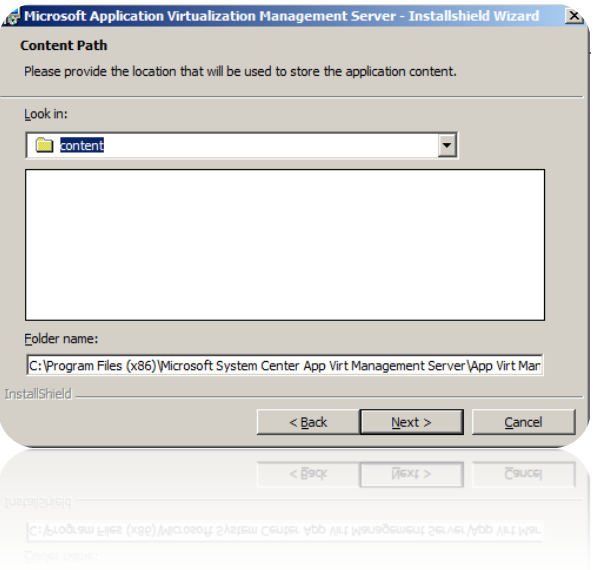
7. Next up is to select where our packages will be stored. This is a bad place to leave the values as default. Its recommended to set a UNC-path – hopefully something placed on a high-capacity fileserver. Maybe using a DFS-path?
If you do not alter this – you will need to change a registry key afterwards. See this KB-article.
So – the default value below is bad. Set a UNC-path.
8. That’s it – kick off the installation and once its done you can restart the computer.
9. Next up is to install a hotfix. KB2007096 is an old article – which still applies to the server. Apply it and get more scalability!
10. Lets continue and check that our database is setup properly. As stated previously – if you install into an existing database – some values will be off. This was first documented by Microsoft as sub-optimal values. If you have more than 100 clients – they are necessary to change.
This is from dbo.Servers
Looks alright – max_conn can be increased to 2000
This is from dbo.SOFTGRID_SERVERS
The important one here is core_timeout should be the recommended value of 120.
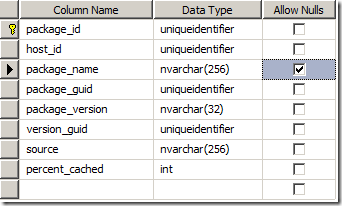
There is one more additional thing to correct before we head out of the database. To resolve some errors when it comes to collecting reporting data. Choose the database dbo.REPORTING_PACKAGE_INFORMATION and select the column package_name. This column should allow NULLs – and then reporting data can be uploaded correctly from the client. Might aswell sort that out before you have any clients upload stuff.
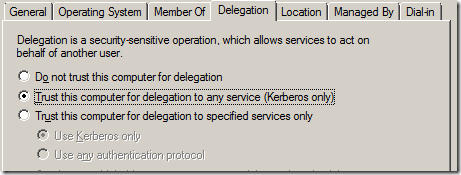
11. Lets head into the exciting part of getting some final details into place. Open Active Directory Users and Computers. Locate the computer-account on which your App-V Mgt Server is running on and ensure that its set to be trusted for delegation – it looks like this;
12. Lets verify the service principal names setup. Since all the components are installed on this one server – we should see; softgrid, MSSQL and HTTP.
This is what is done;
Registered ServicePrincipalNames for CN=WIN-Q1IO4I7IPRU,OU=Domain Controllers,DC
=DCLAB,DC=local:
SoftGrid/WIN-Q1IO4I7IPRU
SoftGrid/WIN-Q1IO4I7IPRU.DCLAB.local
Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/WIN-Q1IO4I7IPRU.DCLAB.local
ldap/WIN-Q1IO4I7IPRU.DCLAB.local/ForestDnsZones.DCLAB.local
ldap/WIN-Q1IO4I7IPRU.DCLAB.local/DomainDnsZones.DCLAB.local
DNS/WIN-Q1IO4I7IPRU.DCLAB.local
GC/WIN-Q1IO4I7IPRU.DCLAB.local/DCLAB.local
RestrictedKrbHost/WIN-Q1IO4I7IPRU.DCLAB.local
RestrictedKrbHost/WIN-Q1IO4I7IPRU
HOST/WIN-Q1IO4I7IPRU/DCLAB
HOST/WIN-Q1IO4I7IPRU.DCLAB.local/DCLAB
HOST/WIN-Q1IO4I7IPRU
HOST/WIN-Q1IO4I7IPRU.DCLAB.local
HOST/WIN-Q1IO4I7IPRU.DCLAB.local/DCLAB.local
E3514235-4B06-11D1-AB04-00C04FC2DCD2/381dfaa1-627f-4bb8-93b3-1da0cc84e89
d/DCLAB.local
ldap/WIN-Q1IO4I7IPRU/DCLAB
ldap/381dfaa1-627f-4bb8-93b3-1da0cc84e89d._msdcs.DCLAB.local
ldap/WIN-Q1IO4I7IPRU.DCLAB.local/DCLAB
As you can see – we are missing the SPN for MSSQL and HTTP (especially if providing icons and OSD via HTTP) – which can be set like this (as an example);
setspn -A MSSQLSvc/WIN-Q1IO4I7IPRU:1433 WIN-Q1IO4I7IPRU
setspn –A HTTP/WIN-Q1IO4I7IPRU.dclab.local
13. Lets go into verifying IIS – as per a quite extensive written article there are some additional topics needed to address to get the final pieces together.
Implement this registry key;
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\HTTP\Parameters]
“MaxFieldLength”=dword:00065534
“MaxRequestBytes”=dword:16777216
Then restart the WWW-service!
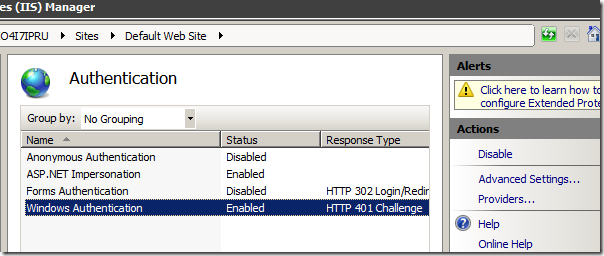
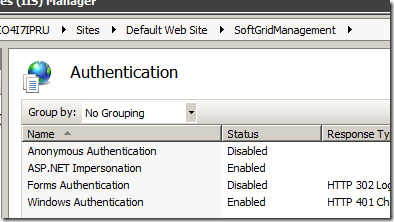
14. According to the same article (as per #13) – we will reverify the IIS-settings. Expand to the default website and lets review the Authentication-settings.
Anonymous is set to disabled and Windows Authentication is set to Enabled. There has been some debate regarding ASP.NET Impersonation – this articlecontradicts what I set. It may be due to the fact that our setup is different – SQL is installed on the same server as the App-V Mgt server. It works if App-V Mgt Server and the SQL server are installed on the same server. If they are not – that might change things. I would suggest to try it with the ability Enabled.
Select Windows Authentication and click Advanced Settings.
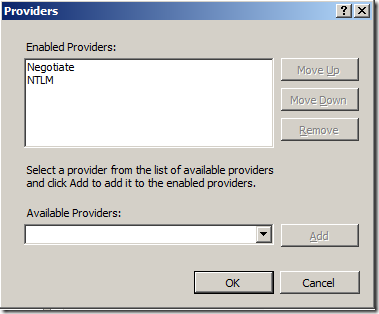
Select Providers and see this;
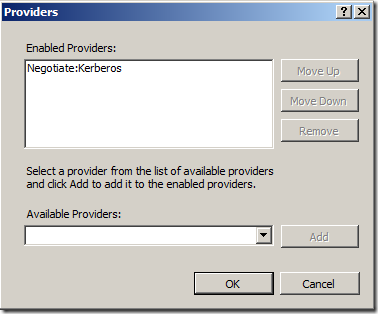
Remove the two that are there and add the Negotiate:Kerberos instead – now looking like this;
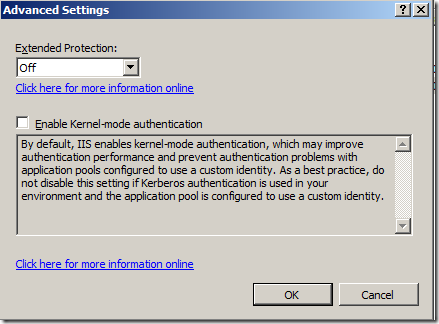
In this setup – “Enable Kernel-mode authentication” was needed to be unchecked.
Select the SoftgridManagement and click Authentication. Lets review there whats set;
These should be very much the same as for the Default Website.
I reviewed the Windows Authentication Advanced Settings and verified that it was set the same as for the Default Website.
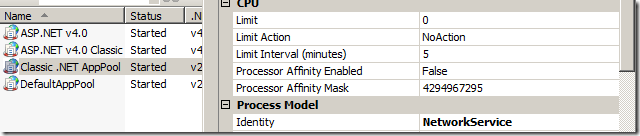
Also – we need to modify the application pool that is used – the Classic .NET AppPool. Since we are using IIS 7.5 – as standard Identity is set to use the ApplicationPoolIdentity. If you attempt to start the App-V Mgt Server Console and connect – you can see a failed login attempt (the dreaded 0000c800 error is only shown from the console itself) by the applicationpoolidentity. Alter this to NetworkService, by choosing AdvancedSettings for Classic .NET AppPool under Application Pools
14. Finally – we have arrived within the App-V Mgt Server Console and are connected. We aren’t done entirely yet… Lets do some configuration tasks within the system itself.
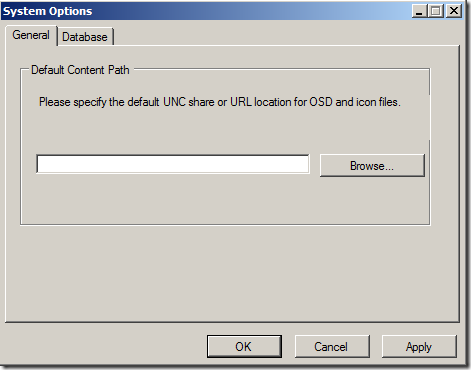
Right-click your host and choose System Options – under the first tab you should the UNC-path to your previously shared folder (step 7)
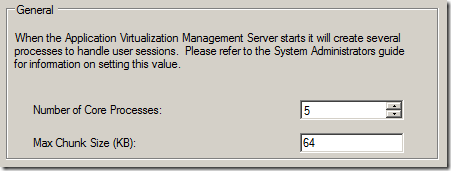
Next is to expand Server Groups and locate your server – right-click it and choose Properties.Go to the Advanced-tab. Now, here we have some options that quite often are left untouched. Lets start at the bottom and work our way up…
Number of Core Processes means how many running processes will be started on this server and therefore streaming applications to users. No idea what the Max Chunk Size value means. So – are those optimal values? With today standards in performance – you can probably increase the number of core processes a lot – lets say 20? However, no performance gain has been seen in doing so. Lets keep them this way.
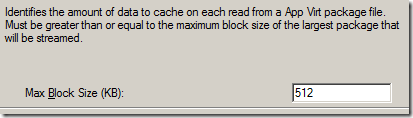
This is the amount of data that is read by the management server each time a request is made for a package. 512 KB is currently pre-read for each streaming operation. This also seems fairly optimal.
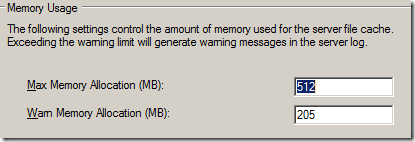
These values are never optimal by todays standards. Justin Zarb wrote an article as to why they aren’t – but essentially the Max Memory Allocation should be set to a number that is the amount of RAM you have – apart from the basic resources the OS needs to operate.
One more additional topic – if you have issues with users not receiving applications because their user accounts are part too many Security Groups. Implement this value;
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SoftGrid\4.5\Server
“MAX_RTSP_HEADER_BYTES”=dword:0000ffff
According to Microsoft – that might help you.
If it doesn’t work (despite all these instructions) – see Aaron Parkers great article.
And if you need reporting – look into this Solution Accelerator.
Not so hard, right?
Updated 2012-08-10;
Actually – I missed some stuff;
There are a couple of new SQL-scripts that are required to be implemented incase you migrate or use a new version of Microsoft SQL Server (anything after 2008 I think..) within the App-V Technet Accelerator Gallery.