As of Parallels Mac Management 4.5 there are great new features – such as the new role Software Update Point.
The addition of this role is to enable managed updates for the OSX-devices within your environment and it acts as a bridge between the Apple Software Update Server (or the able service) and the Configuration Manager environment which PMM integrates into. All of these products will now integrate in a (sort of) seamless way and PMM can now enable its new role (PMM SUP) to inject updates into Microsoft WSUS, which ConfigMgr then uses to publish content. The Apple SUS is optional and if one is setup you can leverage this to further control updates.
Most of this knowledge is based on the Parallels Mac Management for SCCM (bad acronym right there..) Admin guide
Prerequisites
To start using the PMM for SCCM Software Update Point it is required to have a Microsoft WSUS server installed and leveraged for the ConfigMgr environment. Most likely this is already in place if you are already managing updates for Windows-devices.
Allow locally published content
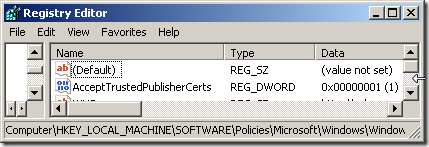
It is required to configure clients to trust locally published content from WSUS. Complete instructions are available from Microsoft, however a quick way to verify if this is setup is to check the following registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
AcceptTrustedPublisherCerts – 1
In addition the signing certificate setup for WSUS needs to be trusted by the client.
WSUS server
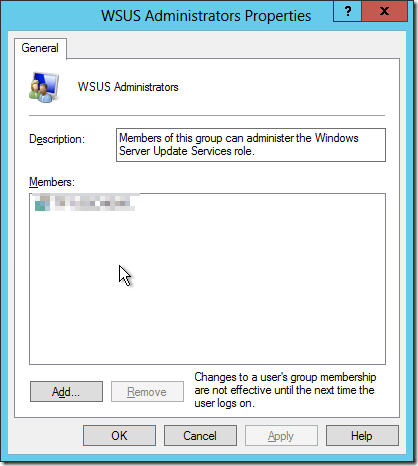
The PMM for SCCM SUP should be installed on server that has WSUS installed (top server in a hierarchy). Before completing that installation a few things needs to be verified. A service account has to be used and configured for the SUP-role, and this has to be a member of the local administrator-group on the server. In addition the service account has to be a member of the local group WSUS Administrators.
Choose Update Server
There are three options when choosing what type of source the Apple Updates should be retrieved from. Basis are:
- Apple Software Updates (public)
Users can choose what updates to install, able to postpone installation and restarts.
Updates will be downloaded from Apple
- Local Update Server (intranet source)
Users can choose what updates to install, able to postpone restarts
- Local Update Server (intranet source) – filtered
Administrators deploys updates
My personal preference is the Apple Software Updates, but incase you want to avoid WAN traffic and potentially more control of updates for your devices the option is a local Apple Software Update Server (or – Local Update Server as stated above). The Apple Software Update Server is part of OSX Server (which can be purchased from Apple Store). Like all other things – this role can be enabled and setup pretty easily. However, it does require an OSX-instance that is running as a server in your environment.
Apple Software Update Server
Once the Apple Software Update Server is setup the PMM for SCCM SUP needs to be configured to direct all requests to this server. A simply registry key edit will finalize the configuration.
These items are only requried to change if you want to use the Apple SUS.
Node: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\pmm_sup_service\Pa rameters
Server Address: SusCatalogBaseUrl
Port: HttpServerPort.
Server settings update interval: InfoUpdateIntervalSeconds
Catalog check: CatalogRefreshIntervalSeconds
The log-file for any activity is generated in the following log-file;
%Windir%\Logs\pmm\pmm_sup_service.log
ConfigMgr configuration
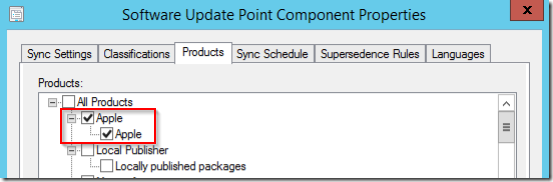
ConfigMgr needs to be configured to synchronize the new Apple Updates. First, update Classifications on the synchronizations properties of the ConfigMgr Software Update Point.
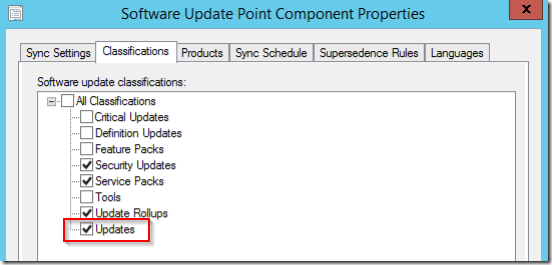
In addition the Apple product needs to be selected.
Client settings
If one is using the public Apple Software Updates there isn’t a need to configure the PMM for SCCM agent as the agent is set to use this source by default. There are three options that can be configured in the following options file:
/Library/Preferences/com.parallels.pma.agent.plist
This matches the previous suggested routes;
0 — Apple Software Update server (default).
1 — Local update server.
2 — Local update server with selected updates.
Set the option :SuCatalogMode to the desired choice in case you need to update it. PMM has realized that their provided Configuration Items are sub-par so in the admin-guide there are script examples (page 134-135) that you can use to create your own Configuration Items.
Summary
Within an environment that already has ConfigMgr, WSUS and PMM setup – the addition of PMM for SCCM SUP isn’t a lot of extra work to enable management of OSX Updates.