![]() iTunes is the ugly step-child (or the Meg, or the bastard) of the Apple family. As iPhone still remains the phone of choice within my family and quite a few corporations there is still a need from time to time to deal with this excuse of a software.
iTunes is the ugly step-child (or the Meg, or the bastard) of the Apple family. As iPhone still remains the phone of choice within my family and quite a few corporations there is still a need from time to time to deal with this excuse of a software.
As a revisit to the previous post where I did track down howto eliminate the end-user requirement to accept the Software License Agreement on corporate installations – there has been some changes in the years past. As the software has decided the progress updates are evil and show no indication of pretty much anything moving this will be how time is spent to track the latest version.
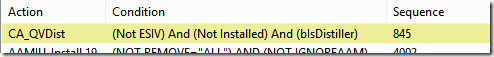
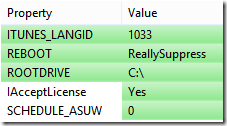
Previously to identify the necessary parts to avoid presenting the SLA for the end-user we required two parts. The first is an identifier for the SLA, and the second was where to put this identifier in the registry.
Registry
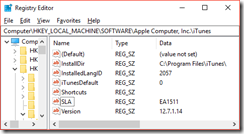
Second things first. The registry key still remains the same. The below is the registry key necessary for a Windows 10 x64 installation of Apple iTunes 12.7.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Apple Computer, Inc.\iTunes] "SLA"="EA1511"
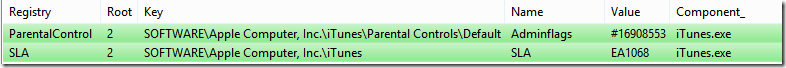
SLA value
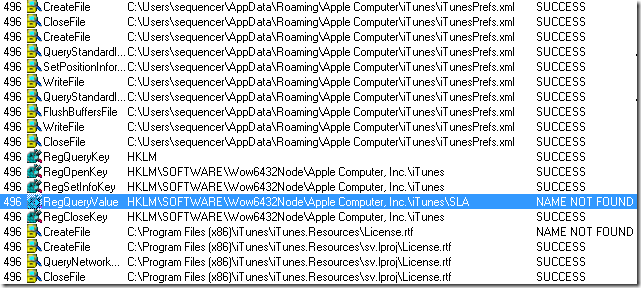
To retrieve the value (EA1511) we need a slightly different process than previously used. The value was stored in iTunesPrefs.xml in the earlier versions of iTunes, however that file doesn’t exist anymore and instead we can see the following files
Opening all of them will reveal binary or hexadecimal-files and neither will allow us to decipher anything we need. As the SLA is most likely located within the installation folder we can poke around and see if the actual SLA will provide us with anything.
Locating the RTF-file License within en.lproj (for english users) could potentially contain something useful.
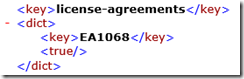
Opening the document and scrolling around it will reveal the two last lines at the bottom of the document
And there it is!