So you have implemented Pulse Secure as a VPN-solution? Well, here are somethings that just about every consulting firm or department eventually will ask you to implement along-side it – so the Pulse Secure client works. The details aren’t here – but more the general mindset, what todo when – but not exactly how every scheduled task / script looks like. Hopefully this will guide you – and potentially arm you with possibility to fix more problems in the future.
Triggers
First things first – a great way to trigger activity is based on Pulse Secure events – described more in detailed on their admin-guide. Common event-ids that might be useful are;
Disconnect – 302 / 106
Connect – 312 (not documented)
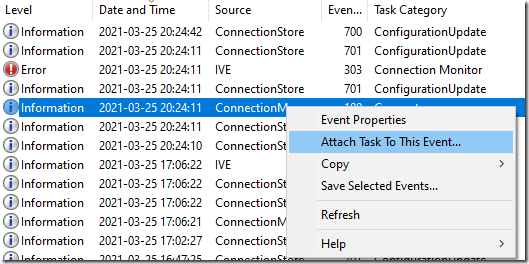
To create a scheduled task for any event – simply find a sample event a select to create a Scheduled Task;
In addition to Application and Services log / Pulse Secure, you can always find Microsoft-Windows-NetworkProfile/Operational. This contains great entries for what network you connect to, what network profile type of profile you connect to. Event-id 1000 within NetworkProfile is simply that you are connected to a new network as a sample.
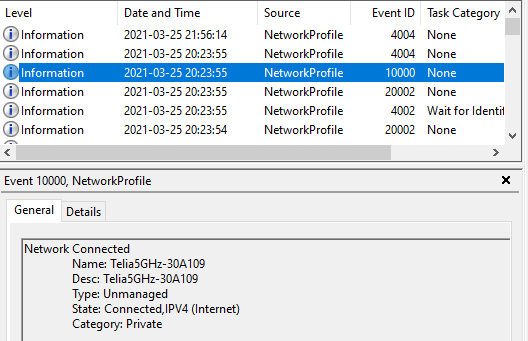
Actions
What actions will be asked to run when these events happen?
Re-register DNS
Name-resolution for the helpdesk not quick-enough to connect to your laptop once you are connected? On event Connect (detected by Pulse Secure/Operational and the event id 312) you can simply have the scheduled task run the command-line – and this will mitigate some stuff.
ipconfig /registerdns
DNS Suffix search list
Pulse normally appends the searchlist of the DNS-suffixes that are set on your client. It also fails to clean this up properly – so name resolution after a disconnect can be challenging. A tidy way todo this would be to trigger on a disconnect (primarily event id 302 within Pulse Secure, but also 106 might be applicable) and then do a sweep. Sample code;
$dnsCGSetting = Get-DnsClientGlobalSetting
$SList = $dnsCGSetting.SuffixSearchList
If ([string]::IsNullOrEmpty($SList) -or $SList -eq "OK.suffix")
{
#donothing
}
Else{
Set-DnsClientGlobalSetting -SuffixSearchList @('')
}
SuperUser has some options if you have a longer list of suffixes to handle..
Host-checker antivirus check
Did someone implement a host-checker and decided something needs to be up-2-date? Like antivirus definitions? Use trigger NetworkProfile with EventID to identify that a device has successfully connected to a network, and then do a check which network – and if not the corporate one – start up the processes to ensure users can avoid having a failed connect.
Sample functions (to check what network and do a validation of Defender AV Signature) – in VBscript as this was to be firing of quite heavily on all endpoints.
Private Function NetConnectionProfileName(Network)
Dim objWMIService
Dim colItems
NetConnectionProfileName = False
On Error Resume Next
Set objWMIService = GetObject("winmgmts:\\.\root\StandardCimv2")
Set colItems = objWMIService.ExecQuery("Select * From MSFT_NetConnectionProfile")
For Each objItem in colItems
if objItem.Name = Network Then
NetConnectionProfileName= True
End if
Next
Set objWMIService = Nothing
End Function
Private Function DefenderSignatureUpdate
Dim objWMIService
Dim colItems
DefenderSignatureUpdate = False
On Error Resume Next
Set objWMIService = GetObject("winmgmts:\\.\root\Microsoft\Windows\Defender")
Set colItems = objWMIService.ExecQuery("Select * From MSFT_MPComputerStatus")
Wscript.echo "Definition-update: " & Left(objItem.AntivirusSignatureLastUpdated,8) & "Today: " & year(now())&right("00" & month(now),2)&right("00" & Day(now),2)
For Each objItem in colItems
if Left(objItem.AntivirusSignatureLastUpdated,8) = year(now())&right("00" & month(now),2)&right("00" & Day(now),2) Then
DefenderSignatureUpdate = True
End if
Next
Set objWMIService = Nothing
End Function
A similiar way within Powershell to detect a Domain-profile is posted on Twitter:
Windows Firewall profile doesn’t always switch to Domain when you use a third-party VPN client
This isn’t really an action. You could most likely trigger something off the event ids – however, Microsoft has documented a great article about this problem. Pulse allegedly fixed this in a really old-version of the client, but to this day noone is happy about it. Set the two workarounds as part of your baseline for devices connecting via VPN – and you should be good. Pulse (now owned by Ivanti) will not be fixing this it seems. As far as I can tell Pulse adds routes, and then doesn’t notify Windows in anyway that triggers a rediscovery for Domain-connections.
Microsoft states:
- First, disable Domain Discovery negative cache by adding the NegativeCachePeriod registry key to following subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NetLogon\ParametersName: NegativeCachePeriod
Type: REG_DWORD
Value Data: 0 (default value: 45 seconds; set to 0 to disable caching) - If issue doesn’t resolve, further disable DNS negative cache by adding the MaxNegativeCacheTtl registry key to the following subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\ParametersName: MaxNegativeCacheTtl
Type: REG_DWORD
Value Data: 0 (default value: 5 seconds; set to 0 to disable caching)
Force a new network-profile
Your client still skipping around and not getting stuff right? Well, you can switch over to a Private Profile. Public is by default, and Domain requires that a Active Directory is reachable (process documented in previous article from Microsoft) – but Private you can switch to.
See this one-liner to detect a specific network and switch the Network Profile
Get-NetConnectionProfile -Name 'networkname' | Set-NetConnectionProfile -NetworkCategory Private